I recently had cause to refer back to a particular organization’s data breach, which occurred in June 2020. The organization is question was Yarooms, who develop room booking software.
I remember reading about a significant breach of Yaroom’s customer data back in 2020, but I wanted to jog my memory as to the nature and extent of the breach.
To my amazement, I could find nothing about this incident through either a Google or a Bing search.
Artificial Intelligence wasn’t much help either…
Yet, I was confident that such a significant breach did occur of Yarooms’ customer data in 2020.
Had I imagined it?
I was beginning to think so… until I found this tweet:
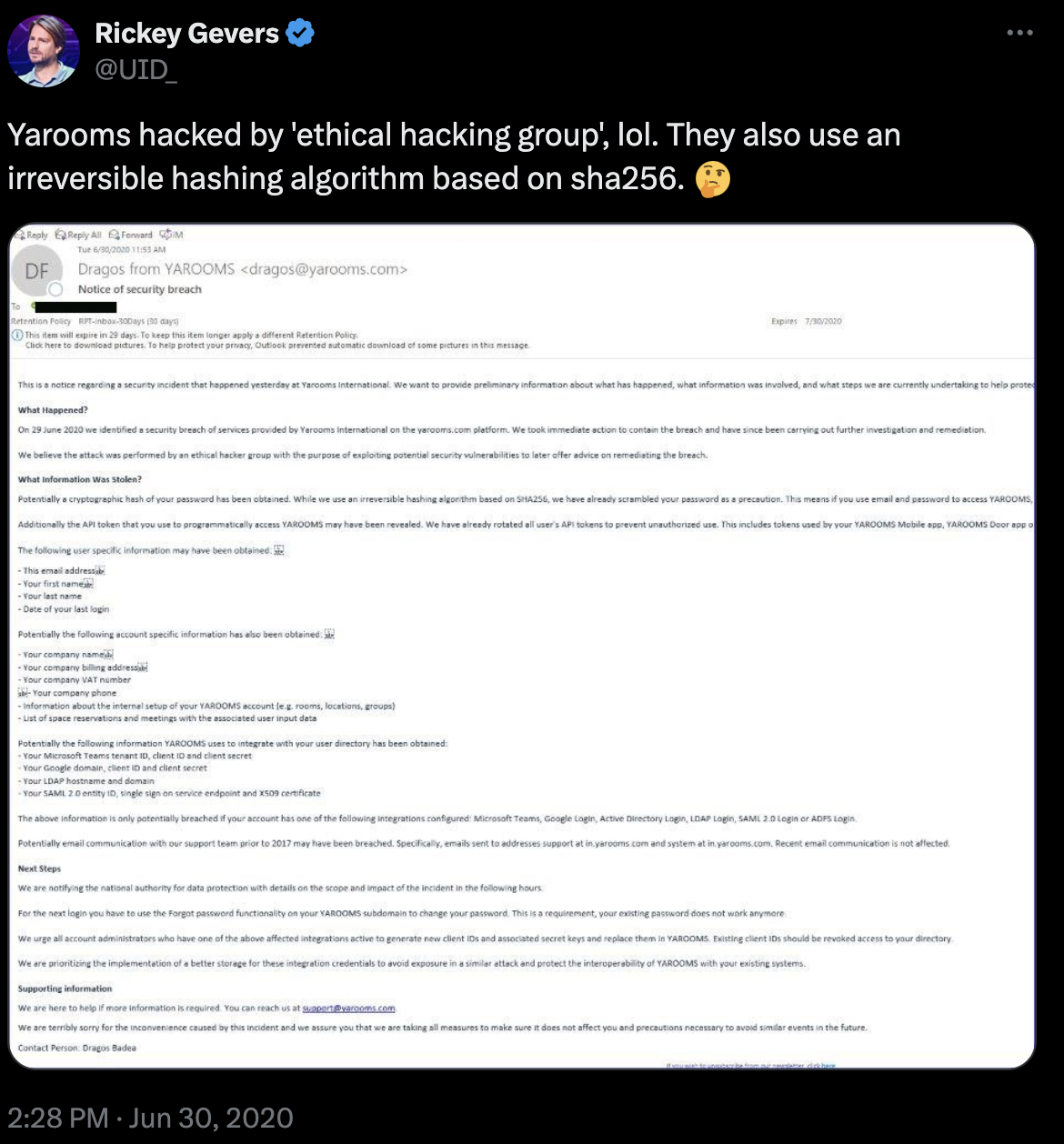
The tweet included a screenshot of an email sent to Yarooms’ customers dated 30th June 2020.
What data was exposed?
Here’s a larger version of the email contained within the aforementioned Tweet:
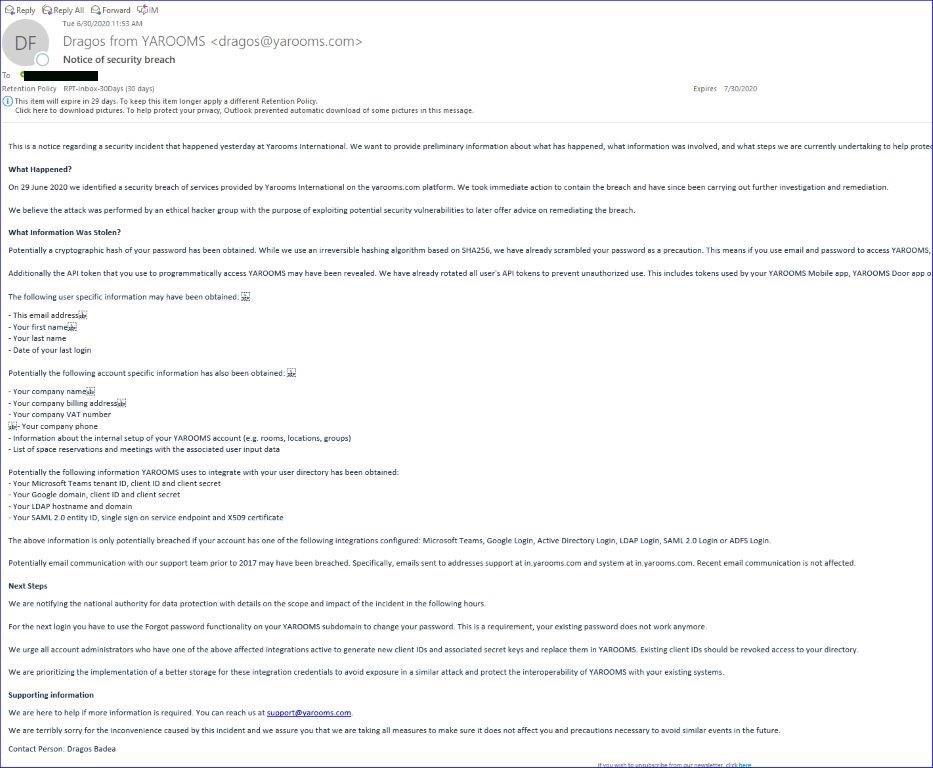
Ok, so it’s a little hard to read, but here are the key points:
- A “security breach” of Yarooms customer data was identified on 29th June 2020
- The following data was exposed:
- A cryptographic hash of users passwords
- API tokens
- Account specific information including company names, billing addresses, VAT numbers, phone numbers
- A customer’s Yarooms setup, including rooms, locations, and groups
- List of space reservations and meetings with the associated user input data
…so essentially, ALL Yarooms customer data was exposed!
But it didn’t end there, the breach also exposed customer’s:
- Microsoft Teams Tenant ID, Client ID, and Client Secret
- Google Domain, Client ID, and Client Secret
- LDAP (Active Directory) hostnames and domain
- SAML 2.0 entity ID, single sign-on service end point and X.509 certificate
Furthermore, the breach additionall exposed all email communication with Yaroom’s support team prior to 2017.
All in all – a pretty significant breach!
Why did you never hear about this breach?
Well, quite simply, Yarooms kept it quiet!
There was no “public” statement put out by them either on their website or elsewhere at the time.
The only communication about this “security breach” was to their own customers via email.
This email did indicate that Yarooms would notify the “national authority for data protection with details of the scope and impact of the incident“. (For reference, Yarooms are based in Romaina), but no public statements were made.
At time of writing this posts, there is no mention of this “security incident” on Yaroom’s website. Yarooms would effecticely like have you believe that it never happened.
But they notified customers… isn’t that enough?
Frankly, in my view – no. They should have put a public statement out on their website and socials for the sake of total transparency.
Yes, it’s important that customers are made aware of security incidents, but don’t potential future customers also have a right to know if there have been any previous “security incidents” at a company they may be interested in purchasing software or services from? Especially when their entrusting that company (and its software) with precious and sensitive data.
So it could be seen that Yarooms are not all that keen for any potential future customers to know about the substantial data breach that occurred just a few years.
Manipulating the narrative
In what could be seen as an attempt by Yarooms to flood search engine results on this topic with “positive” articles and web pages on the general topic of “data breaches” in order to change and control the narrative. These include:
- “Workplace security & compliance” – a page claiming Yarooms helps “Keep your office, employees, and data secure and compliant“
- “A comprehensive guide to information security in the workplace” – which somewhat ironically says “Don’t let data breaches compromise your workplace” and “With one cyber attack happening every 39 seconds, ensuring robust information security in the workplace is paramount“.
- “Practical ways to improve your workplace security” – which states “Enhanced security awareness leads to reduced risks of data breaches“
- “Why HR departments should focus on corporate cybersecurity” – which states “With the increasing number of data breaches and cyber attacks, it’s more important than ever for HR departments to focus on corporate cybersecurity“
- “Creating the Cybersecurity Culture at Work: 10 Best Practices” – which starts “Companies need to create a cybersecurity culture at work to help prevent serious data breaches. Here are 10 practical ways to achieve that goal.“
There’s plenty more too! Yarooms talk a lot about data breaches in various pages, posts, and articles on their website and across their social channels. Yet not one of these mention their own data breach in 2020.
Why the radio silence?
Ok, look, I get that data breaches happen, and when they do, they can be embarrassing to the companies involved.
But the best way a company can respond to such an incident is with total transparency. Be open and honest with everyone (not just your existing customers) about what’s happened, and what you’ve done/are doing to prevent a similar situation arising in the future.
Don’t get me wrong, I have nothing against Yarooms, and I’ve sure that they’ve since taken steps to prevent a recurrence of what happened in 2020.
But I do wish companies wouldn’t try and sweep past data breaches under the rug and pretend that they’ll go away At the end of the day, if you provide a public service then not only should current customers be made fully aware of “security incidents”, but potential future customers should also be able to find out about them too, so that they can make informed choices.
