Back in January, I discovered a serious flaw in the .as (American Samoa) domain registry (nic.as).
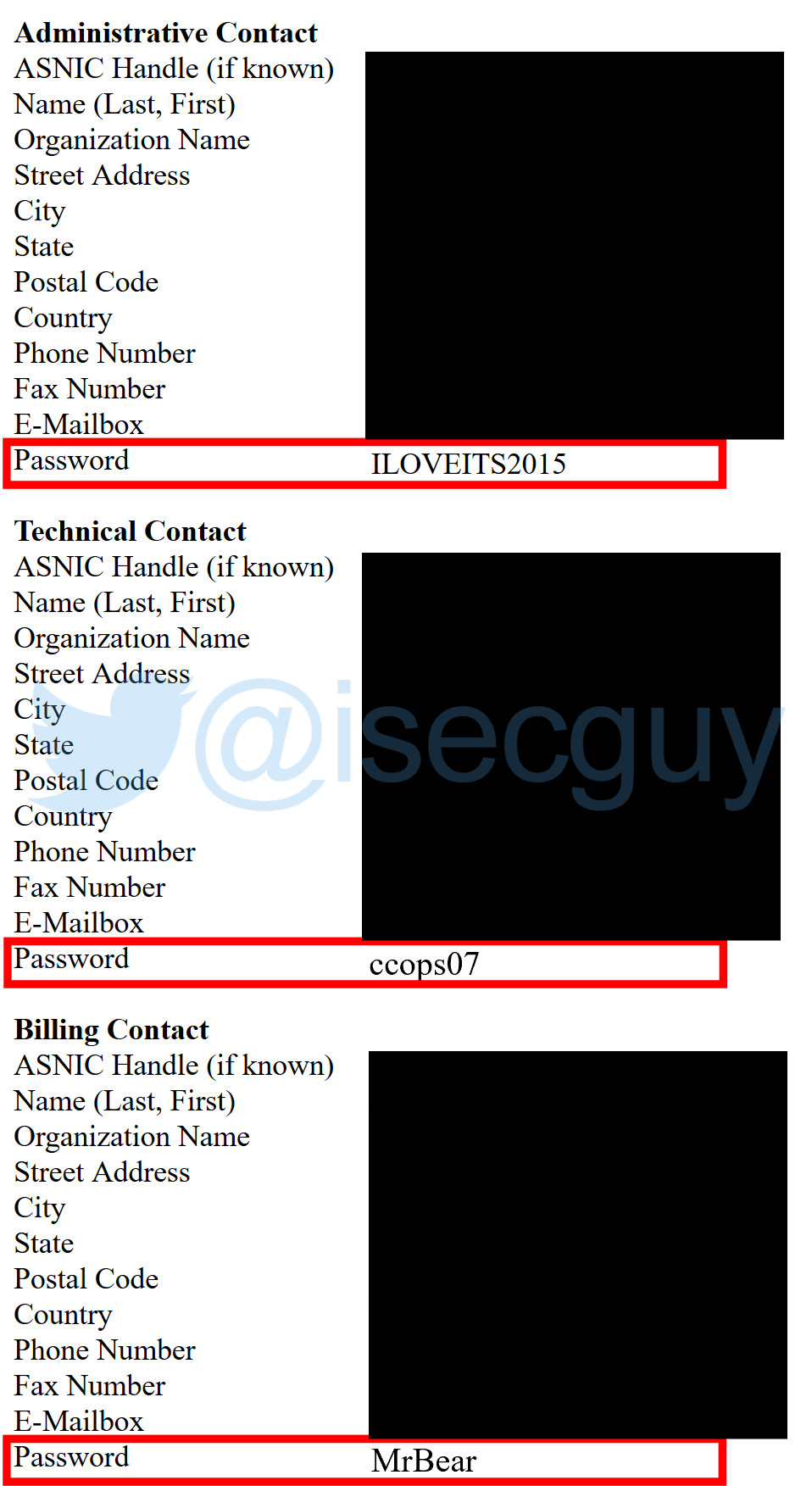
The vulnerability allowed anyone to view the entire domain information for any .as domain – including the plain-text passwords of domain owners, administrative and technical contacts!
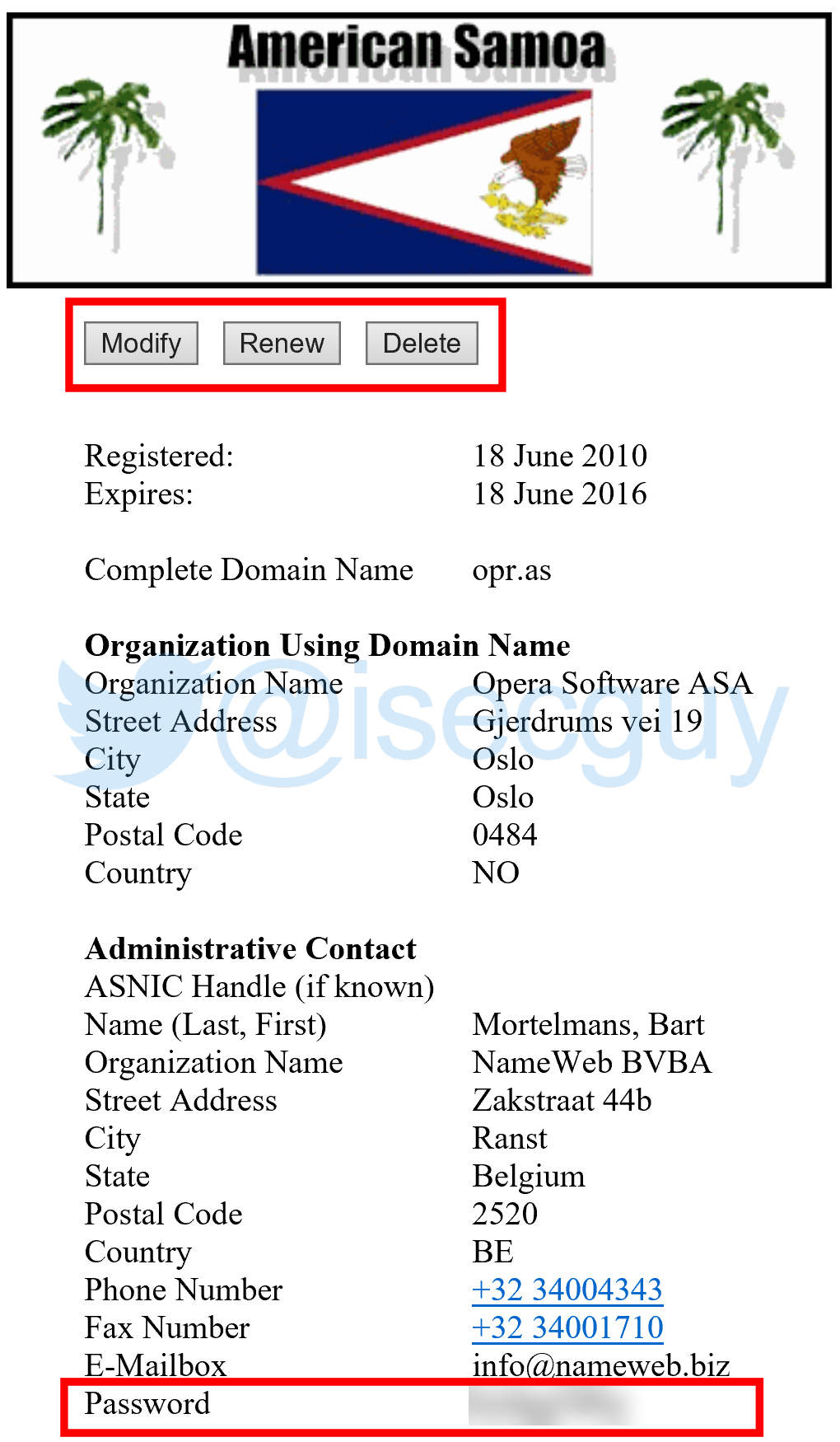
Even more alarmingly, it was also possible to submit registry changes to details held for any .as domain record:
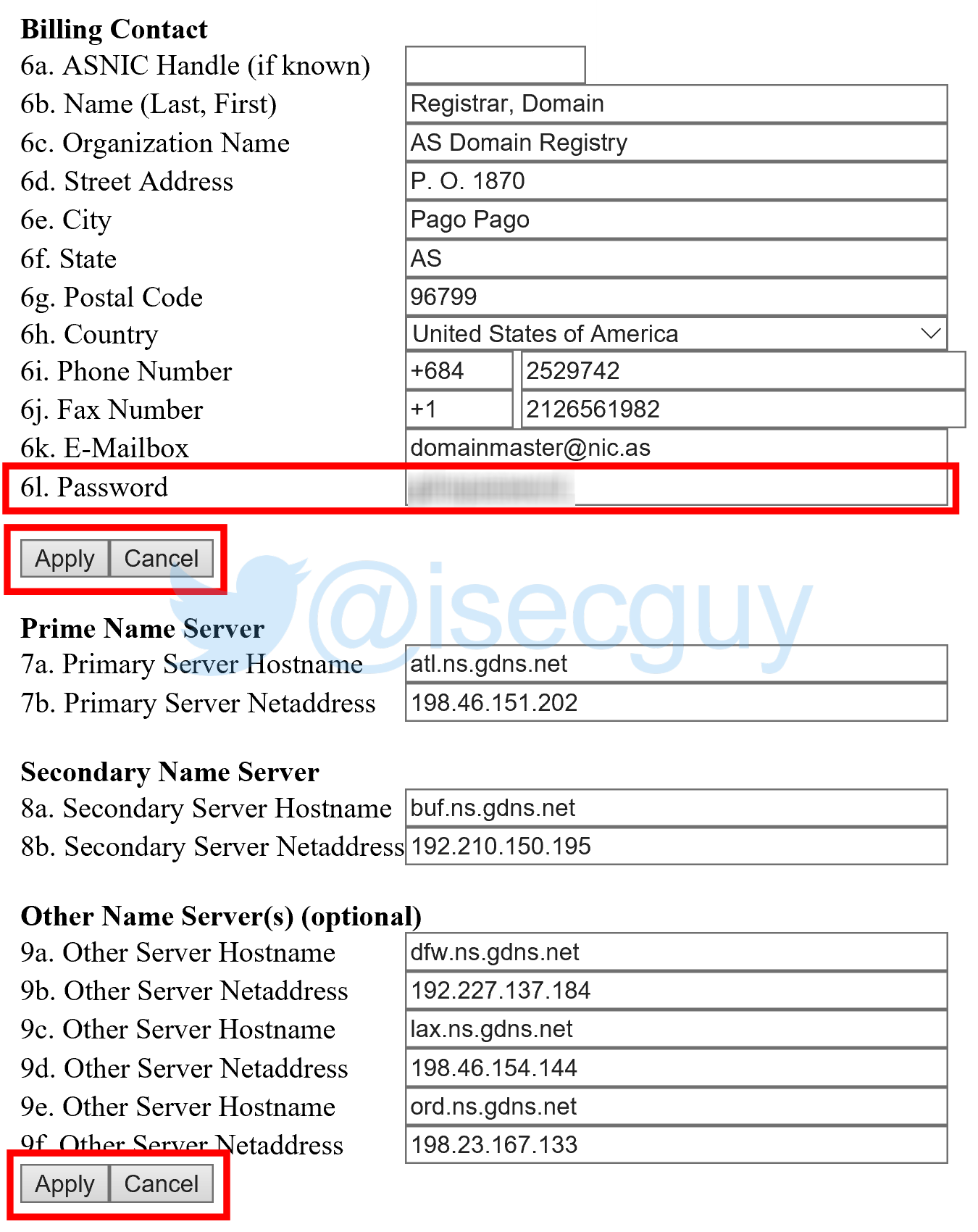
…or even to delete domains entirely!
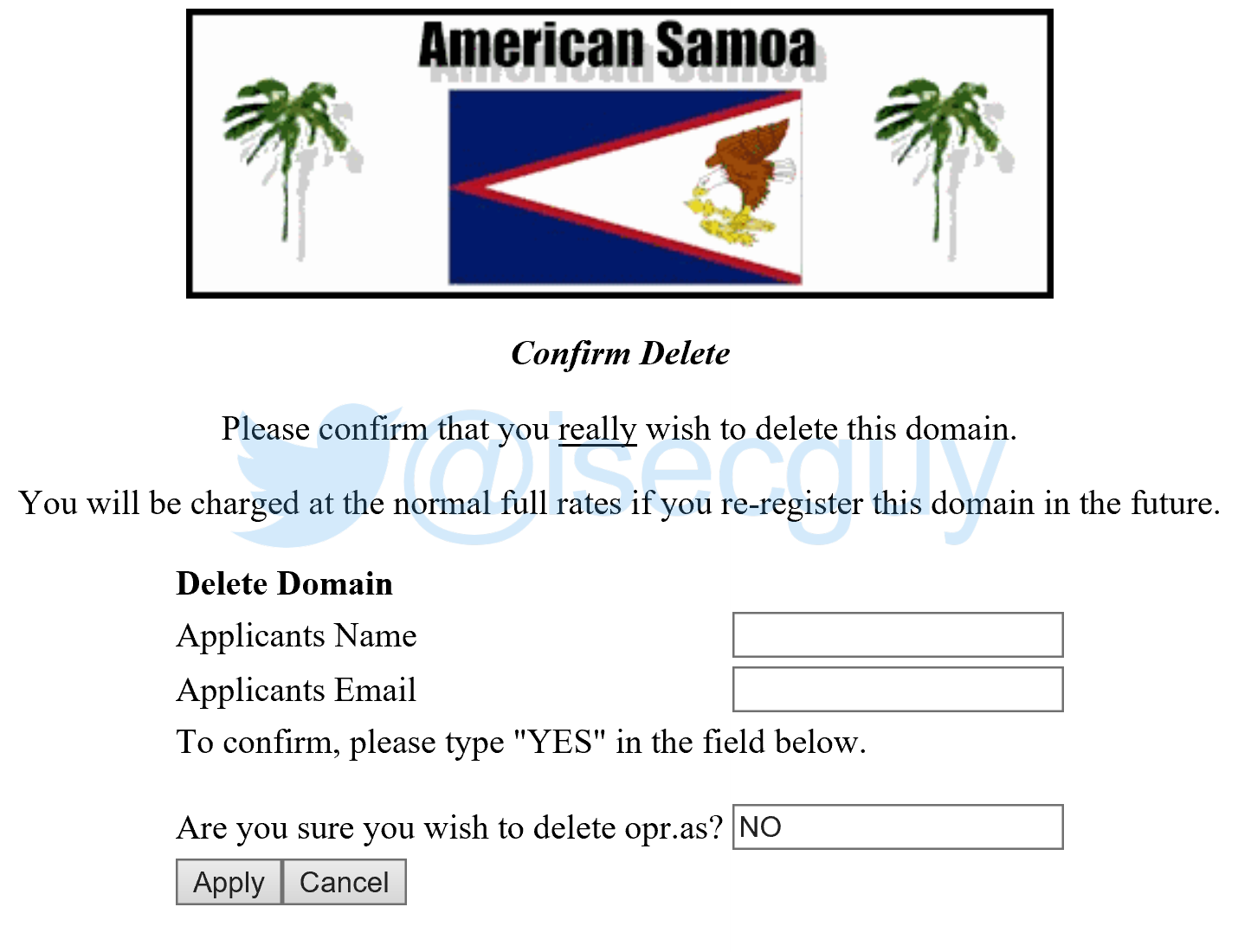
Obviously, this was a very serious flaw – and whilst the .as domain may not be the most popular ccTLD (country code top-level domain), many high-profile and global organizations have .as domain names.
Who does it affect?
Anyone who currently owns (or has ever owned) an .as domain name, or is/has ever been the administrative, technical, or billing contact for an .as domain is affected.
Whilst you may not be all that familiar with the .as domain, its use is far reaching! Here are some examples of .as domain owners:
- Recognizable global brands such as Adidas (a.did.as), Bose (bose.as), Flickr (flickr.as), McDonald’s Australia (macc.as), Opera (oper.as), Twitter (twitter.as), to name but a few all hold .as domains.
- Large educational establishments such as the University of Texas (utex.as)
- American Samoa government institutions including the Department of Commerce (doc.as), and the Office of the Governor (gov.as)
- Link shortening services (such as cbi.as, cort.as and trk.as)
- Other big businesses/brands who use an .as domain as part of a “domain hack” i.e. to form the name of their business/brand name – for example companies like British Gas (britishg.as)
The flaw would allow an attacker to easily take control over these or any other .as domain!
The Flaw
By simply Base64 encoding an .as domain name and appending it to an URL on the nic.as website, it was possible to view the entire domain record for the domain (including unencrypted passwords for domain owners, technical contacts, and billing contacts):
The page also contained buttons to “Modify”, “Renew” or “Delete” the domain:
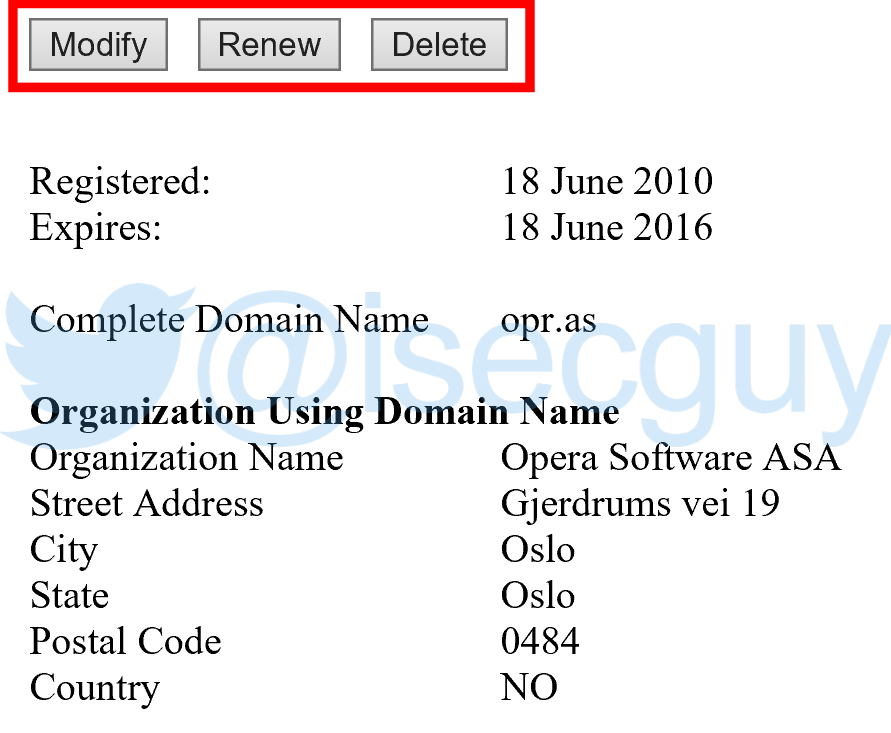
I was subsequently able to verify that it was indeed possible to modify an .as domain record:
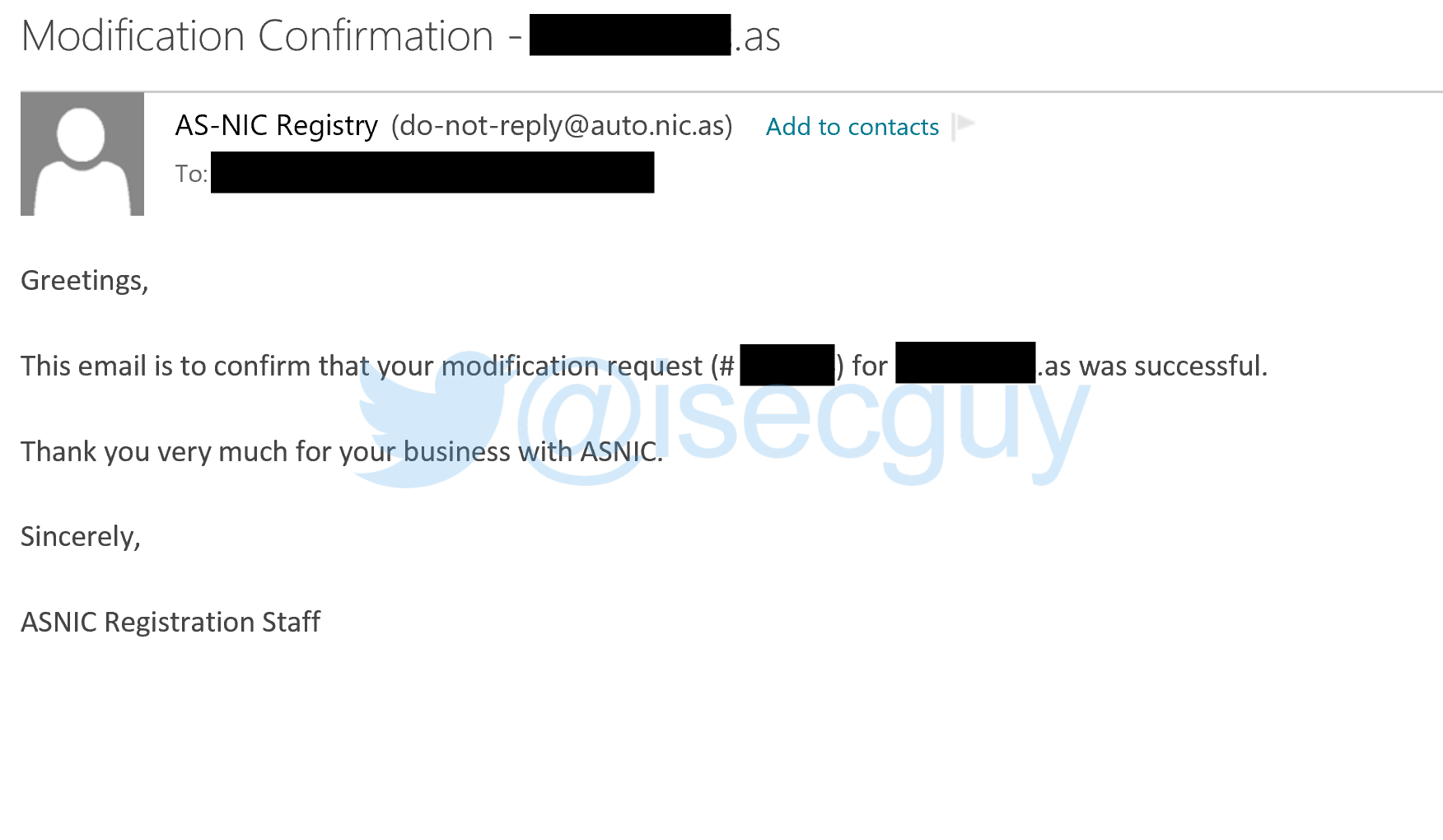
This demonstrated that a malicious attacker could quite easily modify any domain information – such as Nameservers – allowing them to take control of websites by redirecting their traffic to servers they control.
Responsible Disclosure
Upon realizing that not only could I view the plain text passwords for the administrative, billing, and technical contacts for any .as domain name, I could also make modifications, I immediately raised my concerns with the AS Domain Registry on 21st January 2016.
Two days later (23rd January), Stephen Deerhake from the AS Domain Registry “noted” my concerns, but dismissed their severity:
“Your concern is noted. It’s not as big a hole as you suspect; I will drop you an email with an explanation in the morning”
No “explanation” was forthcoming the following day. A week passed by, with nothing further received from Mr Deerhake or the AS Registry, whilst the vulnerability remained unpatched and exploitable.
I contacted the AS Domain Registry again on 1st February to re-iterate my concerns over the serious security flaws in the AS Registry.
The following day, Stephen Deerhake from the AS Registry responded:
“I stand corrected; it is a problem. We expect to have an alternative solution in place within the week. Thank you for bringing this to my attention. It’s very old code (pre-dates the century)”
So not only had the AS Registry backtracked and now acknowledged there was indeed a “problem”, they also indicated that the flaw had existed for over 16 years!
Given this vulnerability had existed for so long, it was highly possible that the sensitive data (including unencrypted passwords) held by the .as registry may have already been previously compromised.
I recommended that the AS Registry notify all .as domain owners, technical and billing contacts to inform them of the vulnerability and that passwords stored by the AS Registry should be considered compromised.
The AS Registry’s response on the 4th Feb was:
“Actually, the password field has never been used. It’s a hold over from the original Network Solutions .com email template from the mid 1990’s”
They were correct – in so much that a password was not required in order for someone to make changes to an .as domain record. However, the fact was that the AS Registry had been storing plain-text passwords and making these visible to ANYONE through this simple flaw (since the mid 90’s!!).
It’s highly likely that .as domain owners, technical contacts, and billing contacts reuse their passwords for other domains they may own – especially when technical/billing contacts are often separate entities (hosting companies, domain registrars, etc) who would manage hundreds if not thousands of domains for their clients.
I again advised the AS Registry that even if the passwords they stored were not used by the AS Registry, there was a very strong chance of “password reuse” by their customers on other sites/domain registries, and therefore the AS registry still had a duty to contact all their customers to prompt them to change their passwords, particularly if these passwords were also in use elsewhere.
A couple of weeks past, and I heard nothing further. I contacted the AS Registry again for an update. On 24th February, Stephen Deerhake from the AS Registry informed me:
“The use of [base] 64 encoding has been eliminated. We are beginning the process of notification.”
A further month passed, and by 24th March, I was aware that .as customers had still not been contacted by the AS Registry about the vulnerability and their exposed passwords.
I reached out to the AS Registry once again to ask for an update as to when the notification process would be complete (so that I could then publicly disclose the vulnerability here in my blog, once all .as customers had been informed)
No further responses have been received to date from the AS Registry.
As of today, 25th April 2016 – over 3 months since I first privately informed the AS Registry of these serious security flaws – whilst they have since fixed the original vulnerability, they have still not reached out and contacted their customers – something which they should have done immediately back in January upon this issue first being brought to their attention.
As I have have no further responses from the AS registry, it appears that they have no intention of ever informing their customers that their passwords should be considered compromised, and are instead trying to keep this all very quiet!
I am therefore today publicly disclosing this vulnerability, and I urge anyone who currently owns, has previously owned, or knows someone else who owns/has owned an .as domain name, to change any password they may have previously entered into the AS Registry that may also be in use elsewhere (especially in other domain registries).
Disclosure Timeline (All times UTC)
- 21st January 2016 09:13 – Responsible disclosure to AS Registry
- 23rd January 2016 07:03 – AS Registry “noted” concern, but dismissed severity
- 2nd February 2016 17:36 – AS Registry finally acknowledge problem and severity
- 24th February 2016 19:31 – AS Registry report flaw has been resolved & customers in the process of being notified
- As of 25th April 2016 09:00 – .as domain owners, technical, administrative, and billing contacts have still not been notified by the AS Registry
- 25th April 2016 09:00 – Public Disclosure
UPDATE – 26th April
A statement has now appeared on the nic.as site:
2016-04-26 PRESS RELEASE – FOR IMMEDIATE DISTRIBUTION
On an anonymous blog today, allegations of a security flaw in the .AS Registry which was supposed to allow anyone to take control of any .AS domain were promoted by the blogger.
Responding to the allegation, Stephen Deerhake, for the AS Domain Registry said today:
“The report is inaccurate, misleading and sexed-up to the max”.
“While it is true that in January of this year we received a report of an issue, that issue related to the legacy registrar system, NOT to the backend Rgistry system. At no time was the Registry system itself in jeopardy”.
“Most domain names in .AS are now managed by registrars using EPP, and this system is not involved in any way. To suggest otherwise is scaremongering.”
Mr Deerhake went on to explain: “We fixed the potential issue back in February with the legacy Registrar system before any problems arose. There was never any potential for unauthorized changes to domain name information, as the Legacy Registrar system is a manual system.”
Whilst the AS Registry did resolve the flaw in February, as acknowledged in this blog post, prior to this it WAS possible for anyone to submit changes to domain name information held in the registry and have these changes approved. Regardless of the registry running a “legacy manual system”, I was able to successfully verify this, and as can be seen from the screenshot in this blog post, received email confirmation of the changes, which I was further able to verify with before and after WHOIS queries.
As the official statement from the AS Registry today clearly demonstrates (and also likely explains why they’ve not felt obligated to notify their customers about this either, despite previously stating they would) – they are even now still refusing to acknowledge the seriousness and severity of this issue!
In relation to the AS Registry’s assertion that this blog post is “scaremongering”; given the reluctance of the AS Registry to communicate with their own customers, this blog post serves to raise awareness among .as domain owners, administrators, billing and technical contacts – who have a right to know that their domains *may* have had unauthorized changes made to them, and passwords compromised over the past two decades this vulnerability has existed for. That’s not “scaremongering” – that’s the responsible thing to do, given that the AS Registry have so far failed to notify their customers.
The knowledge and insight this blog post provides can now enable those .as domain owners, administrative, technical, and billing contacts to take appropriate steps to check the validity of their .as domain record information and change any passwords they may have entered in the AS Registry which they may also be currently using elsewhere on the internet.
The AS registry have had over 3 months now since my initial private disclosure to notify their customers and encourage them to check their domains and change any passwords they may have reused elsewhere. They still haven’t done this, which in my view (and I’m sure in the the view of .as customers as well) is totally irresponsible, hence the reason for this blog post now.
