
Virgin Media are one of the UK’s largest Internet Service Providers (ISP), with over 5 million broadband subscribers.
Yesterday, a concerned Virgin Media customer forwarded me an email they’d received:
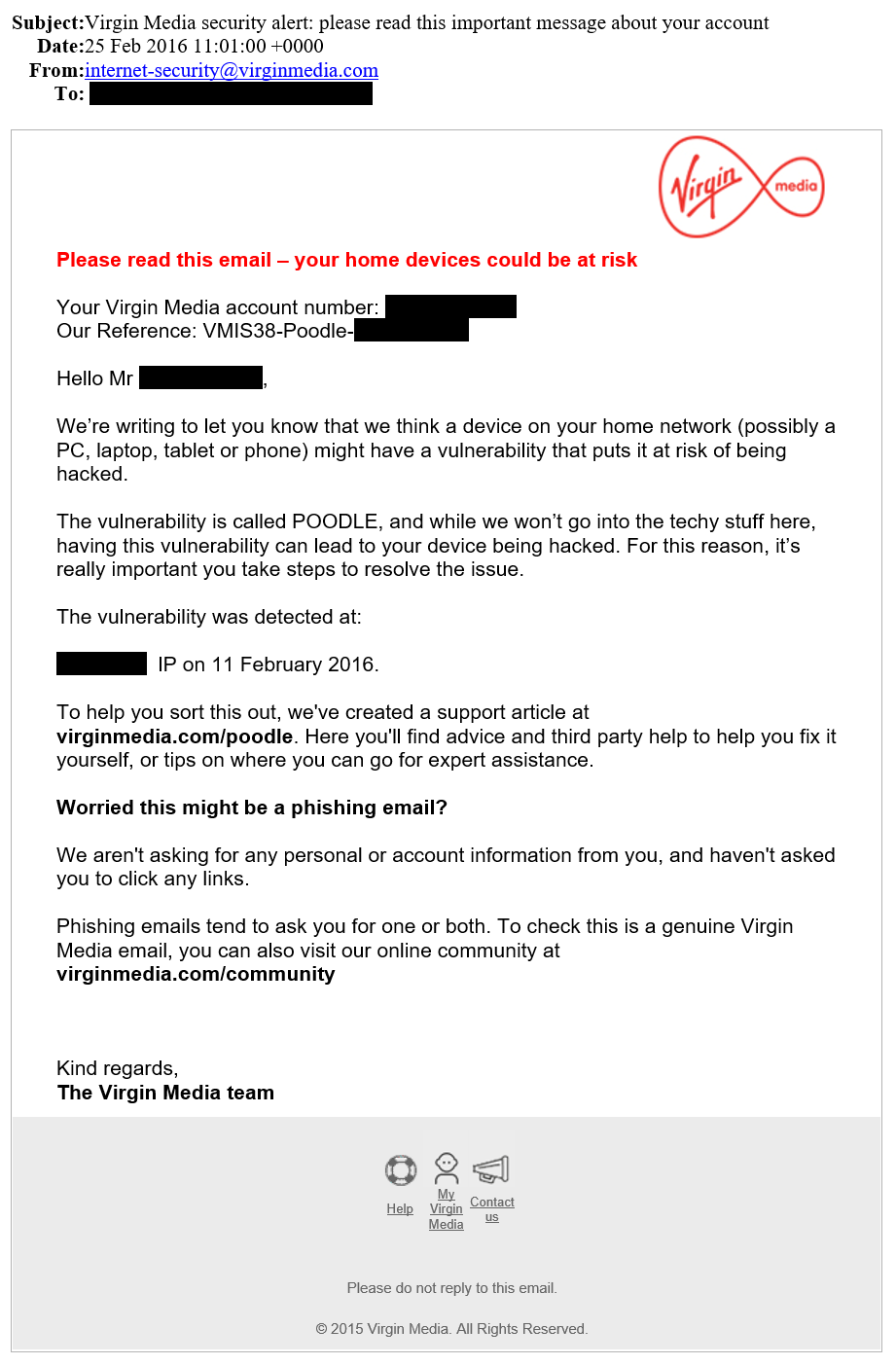
The email – which was addressed to the customer by name, and included their name and IP address – had genuinely originated from Virgin Media. It stated that a device on the customer’s home network “might have a vulnerability that puts it at risk of being hacked“. The customer was naturally concerned about this and reached out to me.
The vulnerability the email refereed to was “POODLE“, which first came to prominence back in October 2014.
In simple terms, the POODLE vulnerability can allow an attacker who already has control over a router/hotspot which your computer, laptop, tablet, or mobile is connected to, to force your web browser to “downgrade” the security of https connections to a less secure variant, which the attacker can then exploit to hijack your browser sessions.
Most web servers on the internet have long since been “patched” against the POODLE vulnerability, and if you primarily browse the web from home, don’t use public hotspots, and your web browser is up-to-date, the potential for damage is very low. None the less Virgin Media felt it necessary to notify this customer that a device on their home network was susceptible, and directed the customer to a page on their website with more information
So was there a vulnerable device on the customer’s home network?
Working with the customer, I was able to determine that port 443 (used for https) was open on their home router, which in turn was port forwarding to a small Windows Home Server residing within their network. It was this server that Virgin Media had detected. As external https access to this server was not required, simply closing port 443 on the router resolved the issue.
How did Virgin Media know there was a vulnerable device on the customer’s home network in the first place?
Virgin Media would have only known about this vulnerability their customer’s home networks were actively scanned or “probed”, a technique often referred to as “port scanning”. “Port Scanning” is when attempts are made to connect to an IP address via a number of different “ports” in order to determine which ports are open, and therefore, which will potentially allow external connections through.
“Ports” allow multiple services to run through the same IP address. For example, when you connect to a website via http, you’re connecting to a server hosting the site over port 80. When you connect to the same website over https, you’re connecting instead over port 443. Other services running on the same server, such as SMTP, IMAP, FTP, etc may also be connected to through the same IP address, but by connecting to a different “port” for each service.
Regardless of their intent, the Port Scans carried out by/on behalf of Virgin Media are an intrusion into their customer’s home networks, and carried out without the customer’s prior knowledge or consent. There is no mention in their Privacy Policy that Virgin Media reserve the right to “scan” their customers networks and store details of devices found.
The help page that Virgin Media point customer’s which they’ve scanned to also contains some revealing and some misleading information.
Firstly, the misleading information…
In the “How do I check if I’m vulnerable?” section, Virgin Media advise you visit a 3rd party site poodletest.com in each web browser on every computer on your home network to determine whether you’re vulnerable to POODLE.
This will be of little help! The issue that Virgin Media have detected on your network will not be due to a web browser on your network per say – it will be due to a device (such as a server or NAS, etc) that listens for connections on port 443. Therefore, you could get an “not vulnerable” response from poodletest.com on all your browsers, as this site only checks your web browser, not your actual IP address and devices on your network.
Secondly, the revealing information….
Virgin Media’s article contains a number of statements that would concern a regular customer who perhaps isn’t all that tech-savvy. Statements like:
- “a 3rd party can use this … to access personal and financial data being sent from your network/devices“
- “…appear to be compromised…“
- “If the vulnerability is not rectified, your personal and financial information could be at risk“
Scary stuff to the average customer!
The article subsequently provides lengthy steps for how to upgrade just about every web browser on just about every device – again, information that may go over the head of the average customer, and even if they did follow all the steps outlined would not resolve the issue anyway, as the issue is not with the customer’s web browser(s).
So, having scared the customer with worrying statements, and providing long and detailed instructions which would ultimately not actually resolve the root cause of the issue, what do Virgin Media suggest the customer does?…
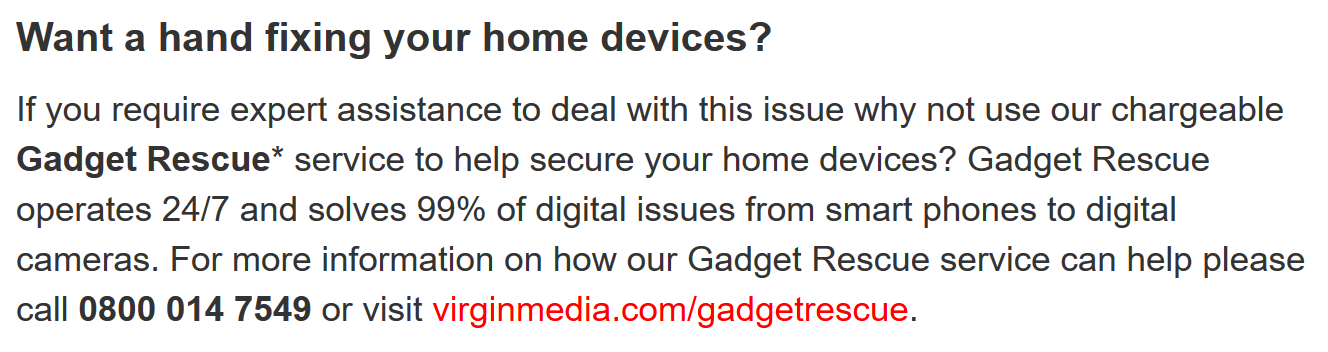
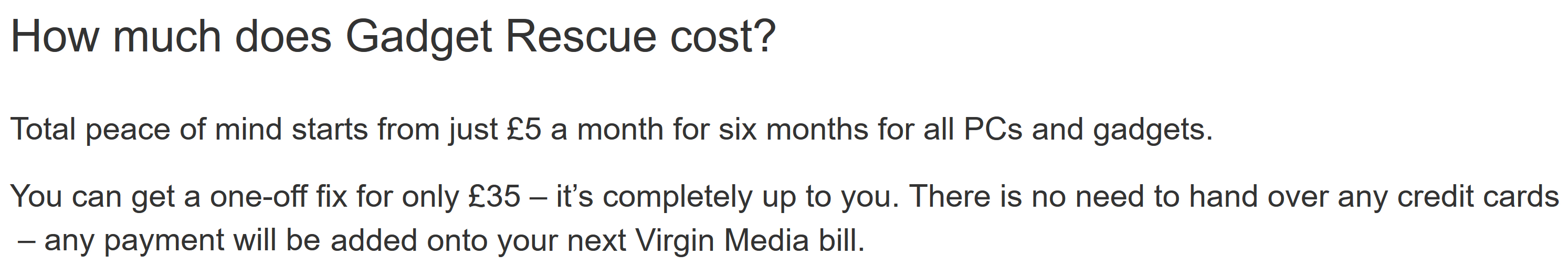
..they suggest the customer uses their chargeable “Gadget Rescue service” to “help secure your home devices“. A service which costs “£5 a month for six months” or “You can get a one-off fix for only £35“
Another interesting point in the case of this particular customer is that Virgin Media detected the “vulnerability” on 11th February, yet waited a whole TWO WEEKS before notifying the customer by email! If this was such a serious security concern for Virgin Media that needed urgently addressing, why the significant delay in sending a notification via email? It appears the “two-week delay” for this customer isn’t an isolated incident – the same delay has also been experienced by other customers, according to VM’s own community forums.
In summary…
- Virgin Media scanned and intruded into a customer’s home network
- Virgin Media waited 14 days before notifying the customer
- “self-help” steps provided to the customer by Virgin Media would not have resolved the issue
- For less tech-savvy customers, resolving the issue would have involved paying at least £30 to Virgin Media
So have Virgin Media secretly been scanning and cataloging devices on their customer’s home networks in order to help improve security? ….or has such activity merely been conducted under this guise, with an underlying intent of “scaring” non-techy customers into paying for their premium “Gadget Rescue” service?
Is it a positive thing that Virgin Media appear to be actively scanning their customer’s home networks & devices, or does this in itself raise security and privacy concerns?
Discuss!
UPDATE 1 – 28th February 2016
Virgin Media customers have been taking to their community forums (1 | 2 | 3) to express their confusion, concern and anger over this issue. Virgin Media have yet to address these concerns, but I’ll update this blog post if/when they do….
UPDATE 2 – 28th February 2016
Security Researcher Paul Moore, has posted this video exploring Virgin Media’s suggested route of using their premium “Gadget Rescue” service in order to resolve the POODLE vulnerability they have contacted customers about:
…as you will hear, the Virgin Media technicians Paul spoke to had no real grasp of what “POODLE” is, or indeed how to correctly/fully resolve it for concerned Virgin Media customers who follow the advice to call and use “Gadget Rescue”!
UPDATE 3 – 29th February 2016
A couple of customers are now reporting on Virgin Media’s forums that they’re receiving these emails from Virgin Media meant for other customers:
FlashPan writes: “I just received this email twice… 1 was for my account and IP while the other was [for] another person/account/IP I am not aware of.“
matt84uk writes: “I’ve had two emails regarding this today – one of which addressed to someone else complete with account number. Not very impressed! Are they giving my details out to other people too?“
Virgin Media have yet to respond to concerns raised by their customers…
UPDATE 4 – 1st March 2016
Security Researcher Paul Moore has posted a lengthy video of Virgin Media’s Gadget Rescue service attempting to “Fix” the POODLE vulnerability they’ve emailed customers about. Bizarrely, their “fix” involves installing Java, Flash, AdBlock+ and Silverlight – none of which address the underlying vulnerability, and far from making your home network more secure, would actually make your device itself LESS secure!
…in short, AVOID VIRGIN MEDIA’S “GADGET RESCUE” SERVICE!!!
