There’s nothing more satisfying that visiting a website and seeing a nice little green secure padlock in your browser’s address bar:
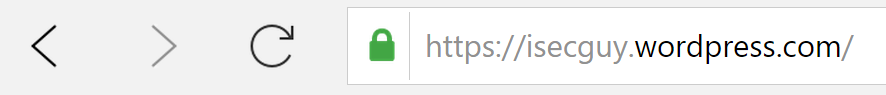
This indicates that your connection to the website is “secure”, and so any forms you fill in on the site (which may contain your passwords, personal or financial information, etc) will be encrypted and can’t be intercepted during transit.
There’s a big push at the moment to encourage all website owners to switch their sites from traditional insecure http to secure https – and rightly so!.
In many respects, Google are leading the way in this…
Firstly, Google’s search engine now looks more favorably on sites which implement https throughout, and gives them ranking priority over insecure sites.
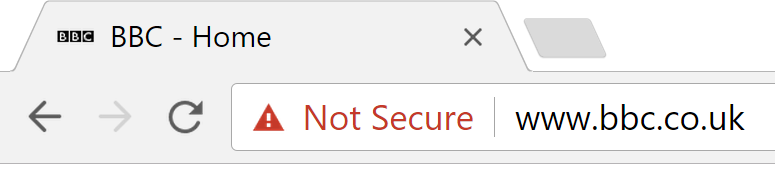
Secondly, Google’s Chrome browser now gives very clear warnings when you’re visiting any insecure sites:
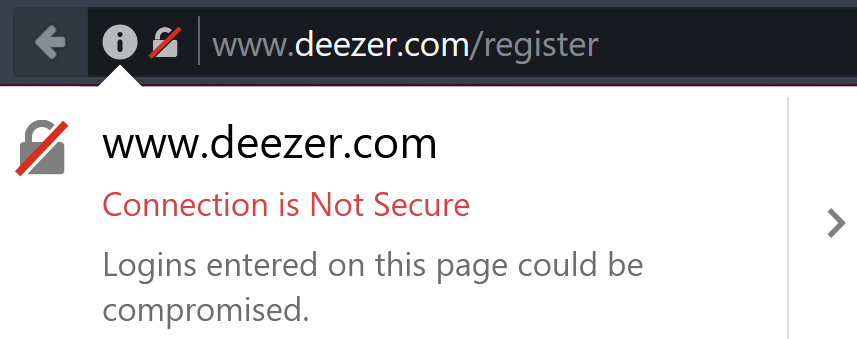
Firefox have also recently made changes to alert you (although not as prominently as Chrome does) if you’re viewing an insecure page which contains a login form (because you should NEVER login over an insecure connection!):
…So it’s clear that https is now becoming the “norm”, and insecure http is very much frowned upon, for obvious reasons!
But what do you need in order to make a website accessible via https? Well, you need to install a security “certificate” for your site. This essentially informs the web browsers of visitors to your site that your site is authentic and therefore to allow a secure encrypted connection between your browser and the website.
If you attempt to connect to a website over https which uses an invalid security certificate, your browser will display all kinds of warnings and errors and will likely prevent you from accessing the site.
Invalid security certificates may be those which:
- Have been misconfigured (i.e. a certificate is only valid for Domain A, yet has been installed on Domain B)
- Have expired – security certificates are only valid for a finite length of time before they must be renewed. If not, they expire
- Have been revoked – a certificate issuer/authority may revoke a site’s security certificate
The majority of website owners obtain security certificates for their web sites via reputable Certificate Authorities (CA).

GlobalSign is one of the world’s most recognized and trusted Certificate Authorities. Established 20 years ago, GlobalSign are the 4th largest Certificate Authority, and currently issue around 10% of all the world’s security certificates.
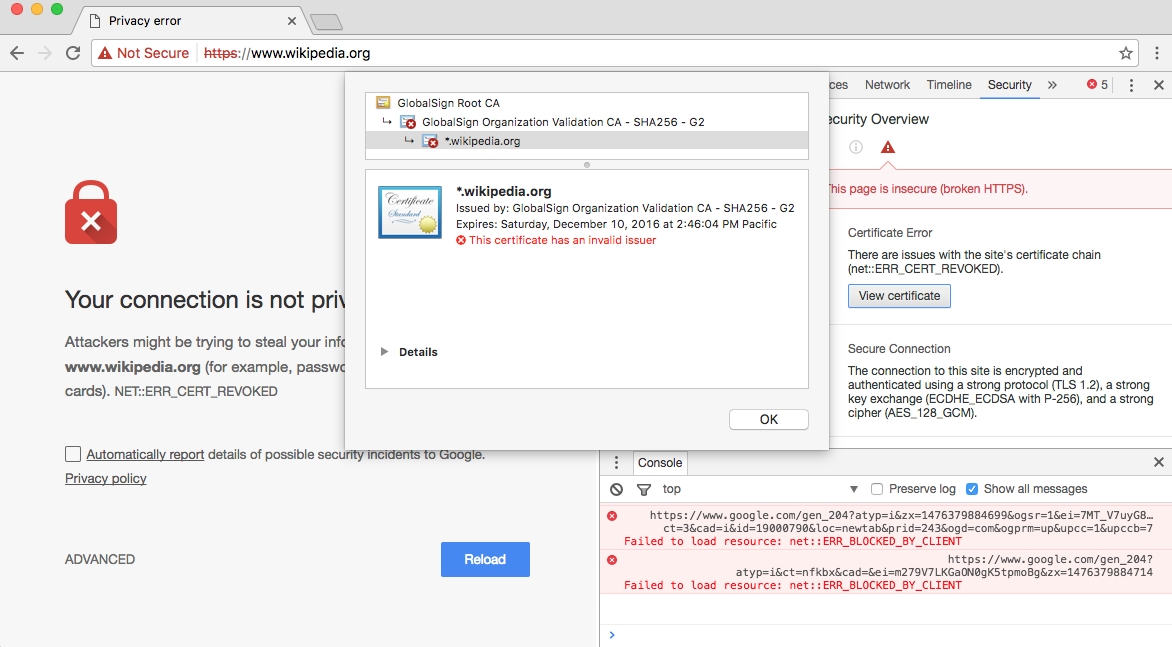
Yesterday, GlobalSign performed some internal maintenance and inadvertently revoked their intermediary security certificates while updating a special cross-certificate. This broke the chain of trust and ultimately nullified security certificates issued by GlobalSign to its customers.
Certificates issued by Certificate Authorities are “cached” around the world, so for many users (who held a cached certificate from before GlobalSign made their mistake) there were no immediate issues, however, for others when they tried to access their favorite websites including Wikipedia, The Times, and more), these returned rather worrying errors about a certificate being revoked:
GlobalSign have since corrected their mistake, however due to the way that these certificates are “cached”, GlobalSign estimate that it could take “up to 4 days” for the issue to fully resolve itself!
GlobalSign have also provided guidance of how you can clear the CRL (Certificate Revocation List) and OCSP (Online Certificate Status Protocol) caches on your local computer, which may help restore your access to affected sites so that you don’t have to wait until next week before you can access them again!
This is a pretty important story! A Certificate Authority can inadvertently revoke a certificate resulting in hundreds of thousands of people being denied access to websites!
It’s not the first time GlobalSign have had significant issues either! In both August and December last year, GlobalSign experienced issues with their OCSP (Online Certificate Status Protocol) servers not responding correctly to requests. This resulted in many Firefox users being unable to access secure sites with GlobalSign-issued certificates, and being presented instead with:
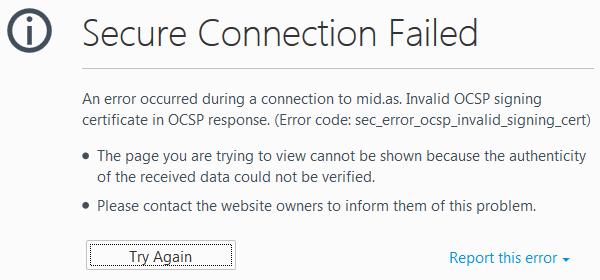
…and if that wasn’t enough, back in 2011, GlobalSign suspended issuing new security certificates for an entire week after an anonymous hacker compromised their servers. It was subsequently determined that only GlobalSign’s own web server was breached and the certificate of this server was stolen. As this server was separate from the certificate-issuing machine (the one holding the company’s root certificate), there was no evidence that any rogue certificates had been issued or any customer data exposed as a result of their breach.
Had there been though, it would have meant that new security certificates would have needed to have been issued and installed on every website using GlobalSign-issued certificates.
By this point, you’re probably forming quite a dim view of GlobalSign. But they’re by no means the only Certificate Authority to experience some serious failings; Chinese certificate authority WoSign came under fire last month for a string of failings, including:
- Back-dating SHA-1 certificates to get around restrictions barring deprecated certs from being trusted
- Mis-issuing certificates allowing arbitrary domain names to be included in certs without validating them
Consequently many vendor/OS vendors (including Mozilla and Apple) now block WoSign certificates.
Summary
Most competent Webmasters strive to do all they can to ensure that visitors to their sites have a safe and secure browsing experience. This includes utilizing https everywhere and choosing a reputable Certificate Authority to issue a security certificate for their site.
Whilst one of the worries in the back of every webmaster’s mind is arguably about falling victim to a hack or having a vulnerability exploited… perhaps we should also be casting an eye over the actions of Certificate Authorities themselves?
As the internet moves towards 100% https – Certificate Authorities need to up their game and start taking their responsibilities seriously!
A “mistake” at their end, or indeed a hack of their systems could potentially impact hundreds of thousands of websites – effectively blocking access to them, or worse allowing malicious hackers to impersonate them.
At the end of the day, there’s only so much webmasters and site owners themselves can do, when their sites are reliant on 3rd party Certificate Authorities.