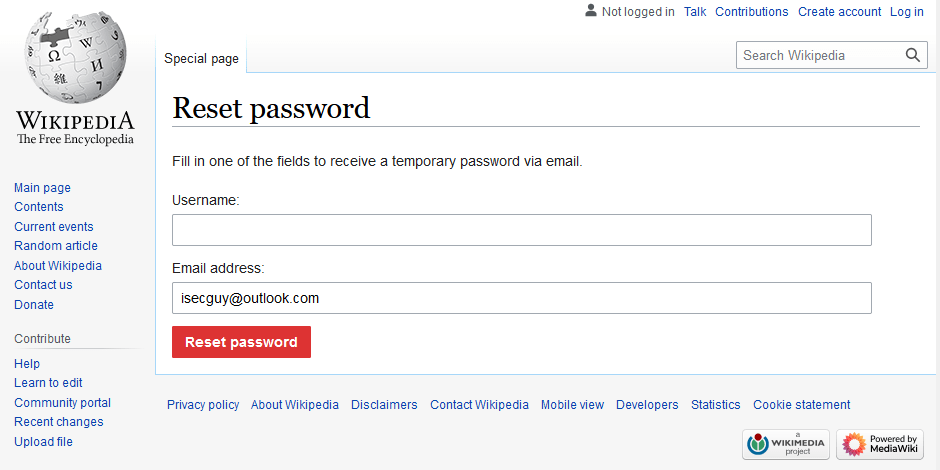
Let’s face it, we’ve all at one time or another had to initiate a password reset on a website we previously registered on way back when and can no longer remember our password.
Yet, I’m frequently amazed at how many websites still get the whole password reset thing very wrong in 2021.
Yes, for the most part gone are the days when if you forgot your password, a website would simply email you your actual password in plain text! (which meant that the website stored and/or had access to your original, unencrypted password, which is a big no-no!)
Thankfully, we’ve moved on from those times. Now if you forget a password you instead have to reset it, as your old password is (hopefully) being securely stored by the website meaning that your original unencrypted password cannot be recovered.
So what are many websites getting wrong with the password reset process in 2021?
Well, it’s all to do with the message displayed on screen when you initially begin resetting your password.
Typically, you’ll be promoted to enter your email address, and click a “Reset my password”-type button…
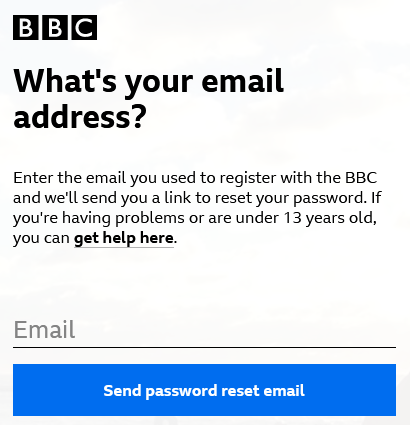
When you click this button, what should happen is that the website displays the exact same message regardless of whether a matching account actually exists.
However, if the website displays a different message depending upon whether a user account with that email address exists or not, then a malicious attacker can use this process to determine whether a person has an account on that particular website.
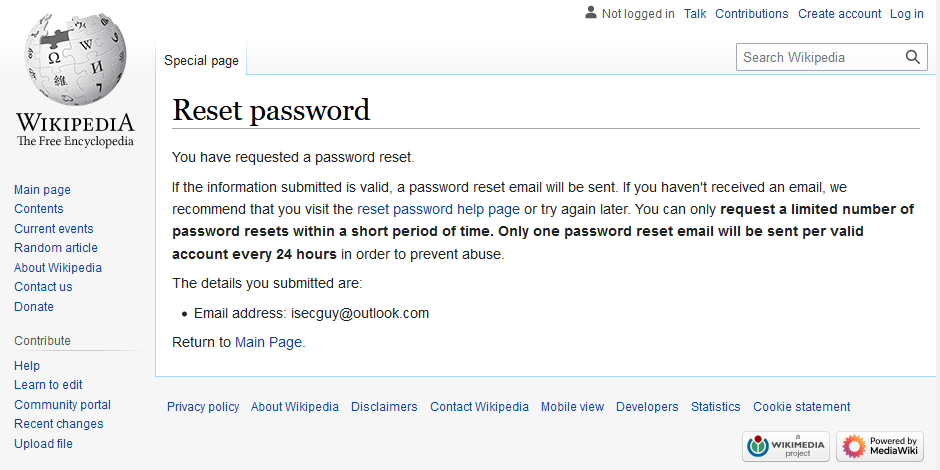
Here’s an example of a site (wikipedia.org) which gets the Password Reset acknowledgement messaging right:
After initiating a password reset request on Wikipedia, the message shown is “If the information submitted is valid, a password reset email will be sent“. This exact same message is shown after initiating a password reset request for either a valid Wikipedia account, or a non-existent one.
This means that it’s not possible for a malicious attacker, given a victim’s email address, to establish whether they have a user account on Wikipedia.
The same, however, can’t be said for many other well-know sites.
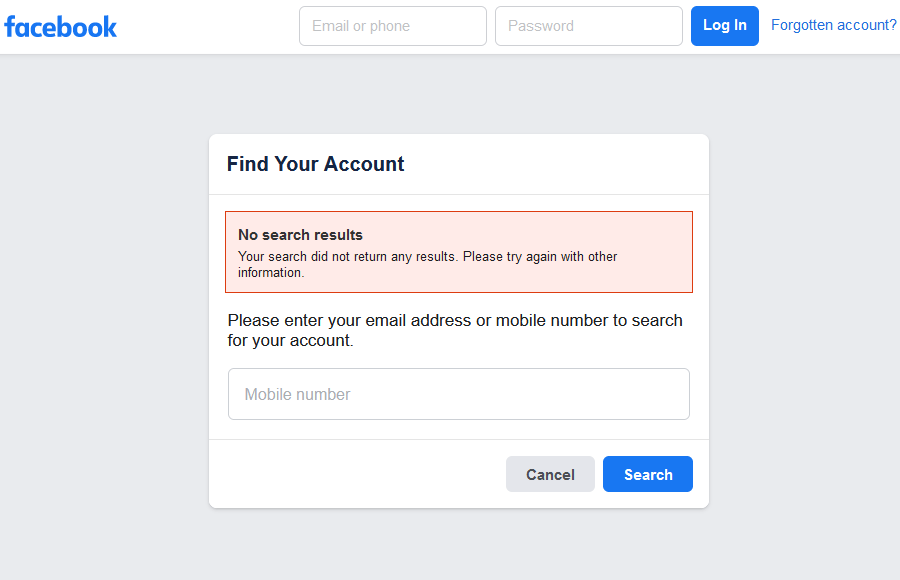
Here are some examples of big name sites that are currently getting password reset request acknowledgements wrong….
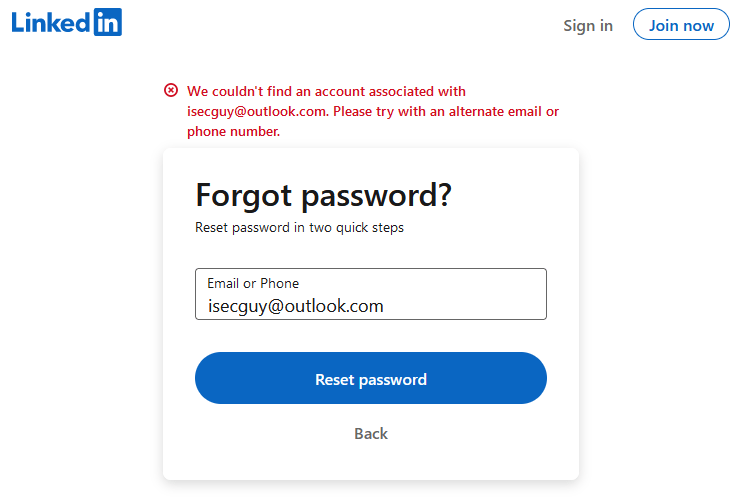
Linked in
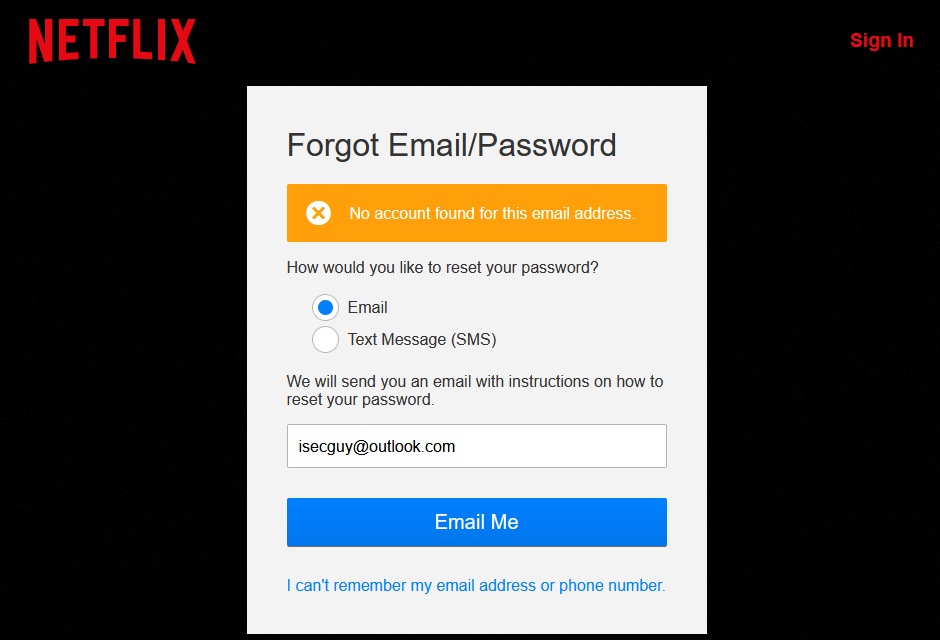
Netflix
BBC
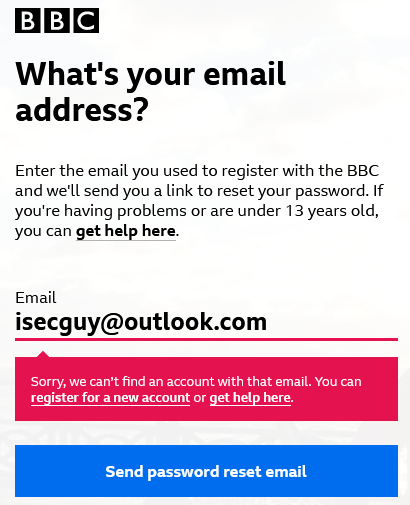
So, knowing just someone’s email address (or in some instances knowing just their phone number) is enough for an attacker – or a stalker – to determine whether that person has an account on major websites.
Now, this in itself doesn’t mean that an attacker can access the user’s account, or indeed reset their password. But it could lead an attacker to craft a very targeted “phishing” attack on the victim by spoofing an email appearing as though it’s from a website that the victim has a valid account on.
In conclusion…
Websites should not disclose whether or not an account exists when processing a password reset request. Doing so allows malicious attackers to determine whether a target victim has an account on that website. Information which could then go on to be used in “phishing” attacks on the victim.
Instead, websites should display an identical and generic message on screen following each password reset request, which doesn’t reveal whether the requested account exists or not.